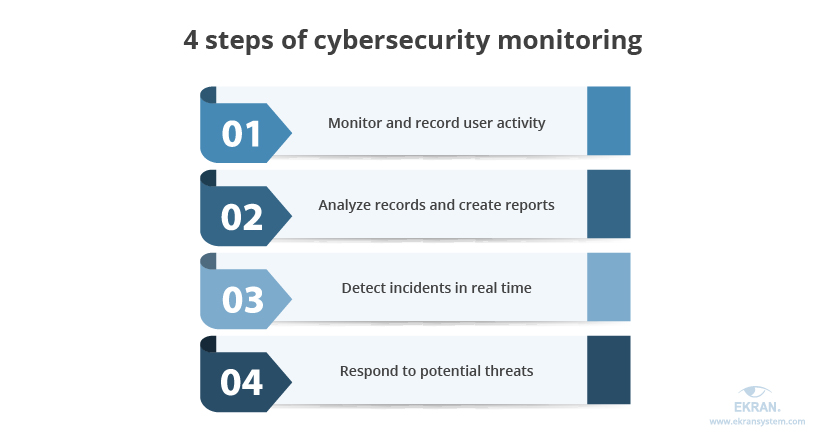
4 Steps to Ensuring Efficient Cybersecurity Monitoring in US Educational Institutions | Ekran System
![PDF] An integrated cyber security monitoring system using correlation-based techniques | Semantic Scholar PDF] An integrated cyber security monitoring system using correlation-based techniques | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/58968c70bbb41db3574ccb48cf74d6a55f4482a3/2-Figure1-1.png)
PDF] An integrated cyber security monitoring system using correlation-based techniques | Semantic Scholar
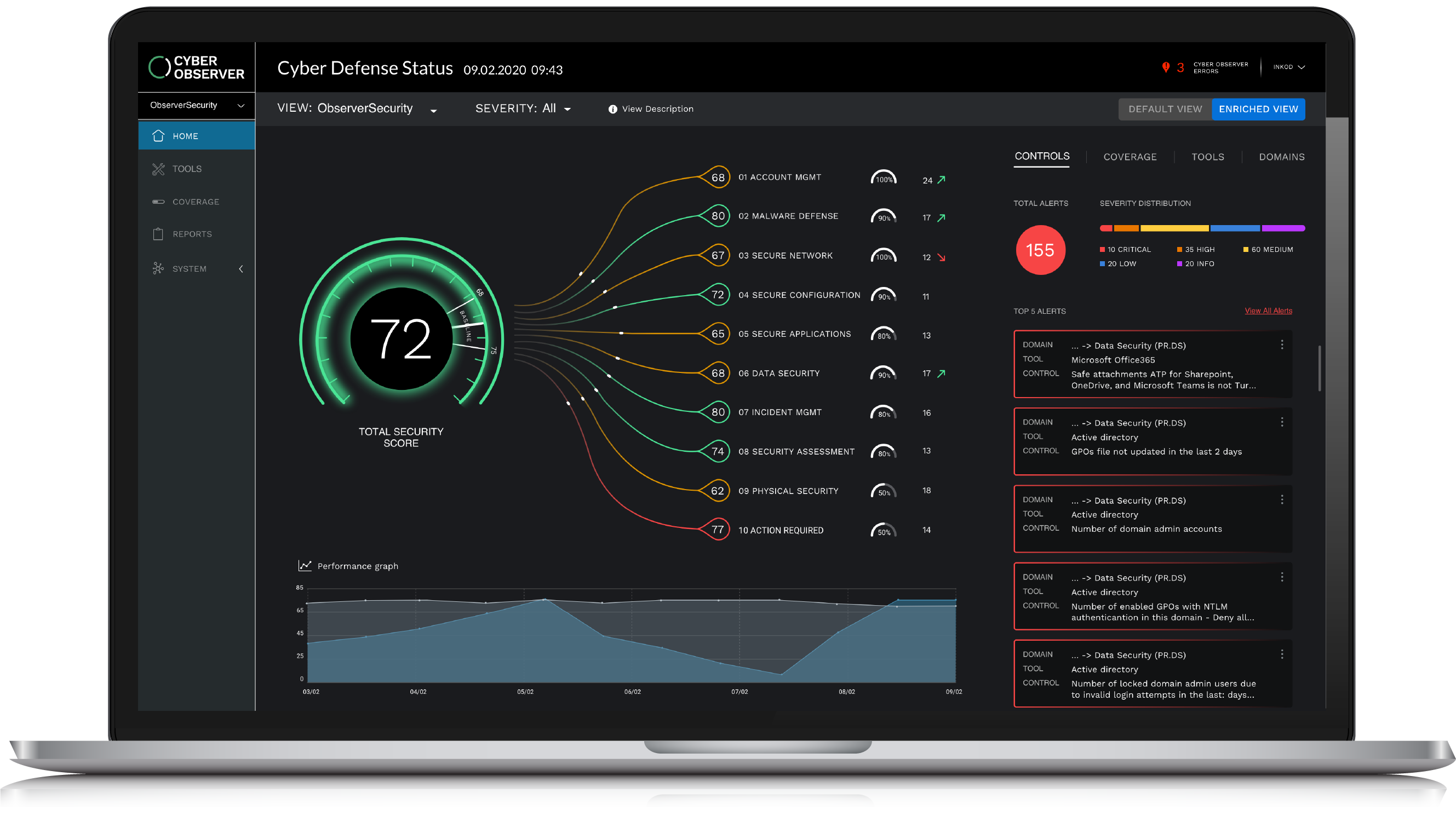
XM Cyber acquires continuous end-to-end cybersecurity assessment startup Cyber Observer - SiliconANGLE























